
The BaroPAM solution is a zero trust security model and is based on the Pluggable Authentication Module (PAM) method that anyone can easily apply to various operating systems and applications that require 2nd authentication (additional authentication) to strengthen the security of information assets. It is a solution that supports multi-layer authentication optimized for security.
The BaroPAM solution is a modular authentication method that does not require a separate authentication server and supports multi-ayer authentication in a decentralized manner, breaking away from centralization. It provides strong security, is simple, requires no management, and has no significant issues. Anyone can easily apply and use it right away. It is a low-cost, highly efficient solution that does not require the introduction of additional servers or DBs when introducing the solution.
1. Desktop Security Requirements
▶Supports multi-layer authentication system using Pluggable Authentication Module (PAM) authentication method that does not require a separate authentication server
▶Uses a globally recognized standard hash function (HMAC-SHA512) and complies with IETF RFC 6238, an Internet security standard
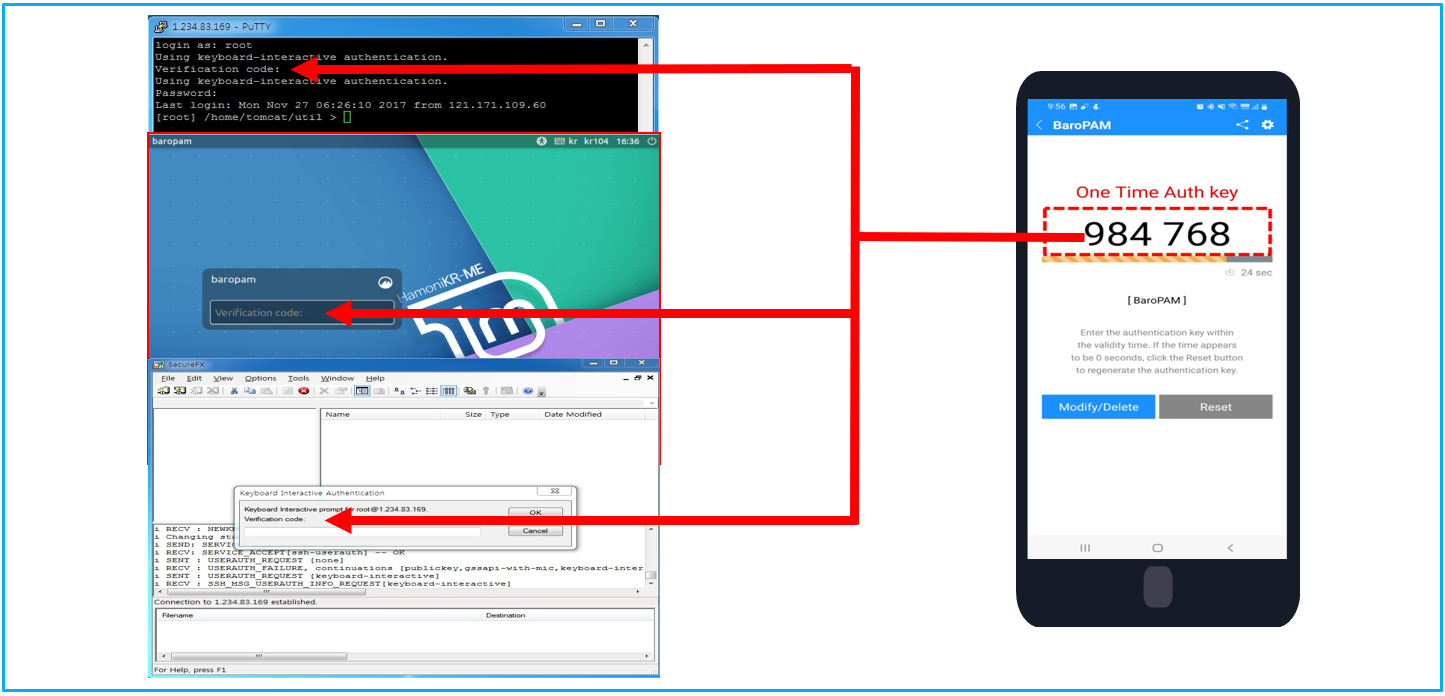
▶OTP authentication is provided in a time-synchronized manner (event and question-and-answer methods are not possible)
▶Authentication is possible even in frequently occurring communication failures or secure areas
▶Provides various simple authentication methods other than OTP code input method. (Mobile, emergency one-time authentication key input, Web OTP, etc.)
▶Provides the ability to individually grant a dynamic secret key and OTP generation cycle (3 to 60 seconds) to desktops (Windows, open OS, Linux, zero and thin client environments, etc.)
▶Provides ACL functionality for accounts that can allow/deny 2nd authentication
▶Provides the ability to limit time and number of times when accessing a desktop
▶Provides the ability to encrypt or encrypt the contents of the configuration file
▶Provides the ability to link environment setting information with a database (MariaDB) in addition to files
▶Provides the ability to detect and block abnormal authentication
▶Provides functions to prevent bypass/remote access blocking and man-in-the-middle attacks
▶Even if your account information is stolen by abusing the automatic login function, you will not be able to log in
▶Even if bypass technology/fatigue attacks and authentication information are forged or altered during the authentication process, bypass authentication is not possible
▶You can start with a simple (loose) configuration and evolve to a more complex (strong) security system
▶If the issued OTP authentication medium is not available, an alternative method is provided to enable OTP authentication. (Emergency one-time authentication key, Web OTP, etc.)
▶Mobile OTP supports Android and iPhone
▶Provides mobile OTP source obfuscation and screen capture prevention functions
▶iOS provides its own identity verification function
▶When executing mobile OTP, a security function is provided to generate an OTP authentication number after biometric authentication (fingerprint recognition, face recognition) or PIN number authentication
▶Provides mobile OTP lock and unlock functions to prevent leakage of OTP information set by others when the mobile is lost
▶Guaranteed full compatibility with currently operating systems

2. Server/Network equipment Security Requirements
▶Supports multi-ayer authentication system using Pluggable Authentication Module (PAM) authentication method that does not require a separate authentication server
▶Uses a globally recognized standard hash function (HMAC-HA512) and complies with IETF RFC 6238, an Internet security standard
▶OTP authentication is provided in a time-synchronized manner (event and question-and-nswer methods are not possible)
▶Authentication is possible even in frequently occurring communication failures or secure areas
▶Provides various simple authentication methods other than OTP code input method. (Mobile, emergency one-time authentication key input, Web OTP, etc.)
▶Provides the ability to individually grant a dynamic secret key and OTP generation cycle (3 to 60 seconds) for each server/account (Linux, Unix, etc.)
▶Provides ACL functionality for accounts that can allow/deny 2nd authentication
▶Provides the ability to limit time and number of times when connecting to a server
▶Provides the ability to link environment setting information with a database (MariaDB) in addition to files.
▶Provides the ability to encrypt the contents of the configuration file
▶Provides the ability to detect and block abnormal authentication
▶Provides functions to prevent bypass/remote access blocking and man-in-the-middle attacks
▶Even if your account information is stolen by abusing the automatic login function, you will not be able to log in
▶Even if bypass technology/fatigue attacks and authentication information are forged or altered during the authentication process, bypass authentication is not possible
▶You can start with a simple (loose) configuration and evolve to a more complex (strong) security system
▶If the issued OTP authentication medium is not available, an alternative method is provided to enable OTP authentication. (Emergency one-time authentication key, Web OTP, etc.)
▶Mobile OTP supports Android and iPhone
▶Provides mobile OTP source obfuscation and screen capture prevention functions
▶iOS provides its own identity verification function
▶When executing mobile OTP, a security function is provided to generate an OTP authentication number after biometric authentication (fingerprint recognition, face recognition) or PIN number authentication
▶Provides mobile OTP lock and unlock functions to prevent leakage of OTP information set by others when the mobile is lost
▶Guaranteed full compatibility with currently operating systems
3. Application Security Requirements
▶Supports multi-ayer authentication system using Pluggable Authentication Module (PAM) authentication method that does not require a separate authentication server
▶Uses a globally recognized standard hash function (HMAC-HA512) and complies with IETF RFC 6238, an Internet security standard
▶OTP authentication is provided in a time-synchronized manner (event and question-and-nswer methods are not possible)
▶Authentication is possible even in frequently occurring communication failures or secure areas
▶Provides various simple authentication methods other than OTP code input method. (Mobile, emergency one-time authentication key input, Web OTP, etc.)
▶Provides the ability to individually grant dynamic secret key and OTP generation cycle (3 to 60 seconds) for each user
▶Provides an algorithm that limits time and number of times for OTP authentication
▶Provides functions to prevent bypass/remote access blocking and man-in-the-middle attacks
▶Even if your account information is stolen by abusing the automatic login function, you will not be able to log in
▶Even if bypass technology/fatigue attacks and authentication information are forged or altered during the authentication process, bypass authentication is not possible
▶You can start with a simple (loose) configuration and evolve to a more complex (strong) security system
▶If the issued OTP authentication medium is not available, an alternative method is provided to enable OTP authentication. (Emergency one-time authentication key, Web OTP, etc.)
▶Mobile OTP supports Android and iPhone
▶Provides mobile OTP source obfuscation and screen capture prevention functions
▶iOS provides a function that allows you to authenticate yourself
▶When executing mobile OTP, a security function is provided to generate an OTP authentication number after biometric authentication (fingerprint recognition, face recognition) or PIN number authentication
▶Provides mobile OTP lock and unlock functions to prevent leakage of OTP information set by others when the mobile is lost
▶Guaranteed full compatibility with currently operating systems
▶A method of linking with the target system must be provided, and considering scalability, provide APIs and technical support necessary for linking with other business systems held in-ouse. (Provides freedom of customization and convenience of development of various applications and integrations)

'▶ BaroSolution > 기술문서' 카테고리의 다른 글
| 사용자 식별.인증을 위한 탈중화 방식의 다계층 인증 시스템 필요성 (1) | 2024.09.22 |
|---|---|
| ‘다계층 인증 체계’ 적용을 통한 안전한 IT 환경 구축 (0) | 2024.09.17 |
| "8자리 숫자 푸는데 단 37초" 충격…내 '비밀번호'도 뚫린다 (0) | 2024.08.27 |
| 랜섬웨어 방어를 위한 다중인증(MFA) 적용은 선택이 아닌 필수 (0) | 2024.08.19 |
| 다계층 인증 솔루션인 BaroPAM 솔루션으로 클라우드의 정보자산 보호 (0) | 2024.08.18 |
